Unlock the Full Value of FinOps
By enabling safe, continuous optimization under clear policies and guardrails

December 9, 2025
December 9, 2025
December 9, 2025
December 9, 2025

Managing multi-tenant Kubernetes clusters requires a deep understanding of resource allocation, security, and scaling strategies. Proper isolation through namespaces, RBAC (Role-Based Access Control), and network policies is crucial to prevent resource contention and security risks. Implementing autoscaling mechanisms for both pods and nodes can optimize resource usage across tenants. Additionally, effective monitoring and logging solutions provide visibility into resource consumption, ensuring fair distribution, preventing overprovisioning, and optimizing costs.
Running multiple tenants in the same Kubernetes cluster seems efficient at first glance, but in reality, it often exposes performance, security, and cost challenges quickly. Teams expect consolidation to simplify operations, yet they end up dealing with tenants competing for CPU, noisy-neighbor effects, and gaps in policies that weaken isolation.
The issue is common across the industry. According to the 2024 CNCF report, 93% of organizations are using or evaluating Kubernetes, but multi-tenant environments still struggle with resource contention, uneven scaling, and configuration drift.
These problems add operational risk and unnecessary cloud spend unless you control how tenants share and consume cluster resources. This is where solid multi-tenant design principles make a real difference.
By understanding the limitations of multi-tenant Kubernetes and applying the right solutions, you can reduce complexity, lower risk, and improve overall efficiency. In this blog, you'll explore how to make multi-tenant Kubernetes work effectively for your organization.
Kubernetes multi-tenancy is the practice of running multiple workloads or applications from different teams or customers (tenants) within a single Kubernetes cluster, while maintaining strict logical isolation and independent resource management for each tenant.
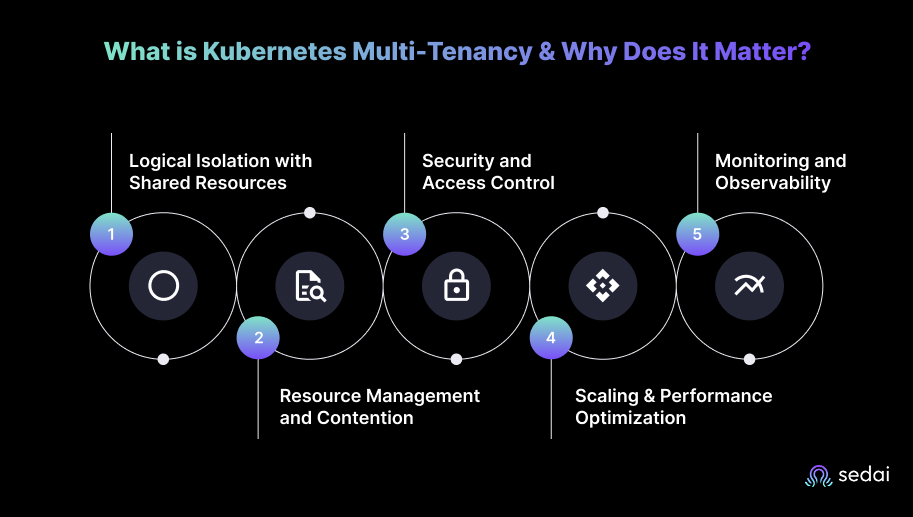
This model allows organizations to share infrastructure efficiently, improving utilization and reducing operational overhead. At the same time, it demands strong security, resource allocation, and workload isolation strategies to ensure performance and reliability are not compromised.
For example, internal SaaS platforms often consolidate multiple teams on a single cluster to reduce costs. But without proper isolation and quotas, one team’s experiments can spike CPU usage, slowing production workloads.
Here’s why Kubernetes multi-latency matters:
In multi-tenant Kubernetes, tenants share a single cluster while remaining logically isolated via namespaces. Each namespace allows independent management of resources like CPU and memory, but Kubernetes does not enforce strict isolation by default.
You must configure resource quotas, limit ranges, and RBAC to prevent tenants from interfering with each other’s resources or security.
Resource allocation is critical in a multi-tenant Kubernetes environment to prevent any tenant from consuming disproportionate resources. You should set resource requests and limits on containers and define quotas per namespace to prevent contention. Without these controls, tenants can unintentionally impact each other’s performance.
Sharing infrastructure introduces security challenges in multi-tenant Kubernetes. Implementing RBAC ensures that tenants access only their own resources, while network policies isolate pod-to-pod communication.
PodSecurityPolicies enforce container security, such as preventing privileged containers. You must rigorously configure these policies to prevent unauthorized access and maintain robust security.
Performance can degrade if tenants over-consume resources. You can optimize workloads with Horizontal Pod Autoscaling (HPA) and Vertical Pod Autoscaling (VPA), which automatically adjust resources based on demand.
Cluster autoscalers allow the cluster to add or remove nodes as needed. Proper scaling strategies maintain performance while avoiding resource waste.
Monitoring is essential to track resource usage and ensure tenants stay within limits. Using tools, you can create tenant-specific dashboards for metrics such as CPU, memory, and network usage.
Centralized logging with ELK Stack or similar solutions helps detect issues, enforce resource limits, and ensure smooth operation across tenants.
Once you understand the importance of Kubernetes multi-tenancy, it’s useful to examine the challenges it presents and the solutions available to address them.
Implementing Kubernetes in a multi-tenant environment delivers significant benefits in resource optimization and cost efficiency, but it also introduces challenges and limitations. You need to understand the key obstacles and know how to address them effectively for maintaining performance, security, and scalability.
In multi-tenant Kubernetes clusters, resource contention is a critical challenge. When tenants share the same physical infrastructure, workloads from different tenants can compete for CPU, memory, and storage, potentially degrading performance if they are not properly isolated or allocated.
Key solutions include:
Monitoring pod-level resource usage and node-level metrics helps identify noisy tenants before they degrade cluster performance.
Although Kubernetes provides logical isolation via namespaces, sharing physical resources introduces security risks. A compromised tenant could affect other tenants if proper isolation measures are not enforced. Ensuring strong security across all tenants is vital to prevent unauthorized access and workload interference.
Key solutions include:
Even with service mesh, misconfigurations in RBAC or network policies can allow lateral movement. Continuous audits are essential.
Providing visibility into resource usage, performance, and security for each tenant is challenging in multi-tenant environments. Without effective monitoring, bottlenecks or security issues can go undetected, potentially leading to operational disruptions or breaches.
Key solutions include:
Scaling a multi-tenant Kubernetes cluster requires balancing multiple tenants’ demands with available resources. As workloads fluctuate, you must scale efficiently without over-provisioning or compromising performance.
Key solutions include:
Avoid scaling too aggressively without monitoring actual usage, as over-provisioning leads to wasted costs and unnecessary operational complexity.
Multi-tenant Kubernetes clusters introduce operational overhead, especially as the number of tenants grows. Maintaining consistency and preventing configuration drift becomes increasingly challenging.
Key solutions include:
Tracking and allocating costs across tenants in a multi-tenant cluster can be complex. Without visibility, some tenants may consume disproportionate resources, causing unexpected cost spikes.
Key solutions included:
Assigning tenant-level chargeback or showback reports encourages teams to optimize their workloads and prevents hidden overspend.
After understanding the challenges and solutions of multi-tenant Kubernetes, it’s helpful to compare single tenancy and multi-tenancy to see how they differ.
Suggested Read: Buyer’s Guide to Kubernetes Optimization
Single-tenancy in Kubernetes provides complete isolation but comes with higher infrastructure overhead and potential resource underutilization. Multi-tenancy, on the other hand, allows resource sharing, improving cost efficiency and scalability, but demands strict controls to prevent security risks and performance issues.
Below are the key differences between single-tenancy and multi-tenancy.
While multi-tenancy reduces infrastructure costs, the operational overhead and need for strong monitoring often outweigh savings for small environments. Evaluate trade-offs before consolidating clusters.
Once you are clear about the differences between single and multi-tenancy, you need to have a look at the different types of multi-tenancy architecture.
When configuring multi-tenancy in Kubernetes, you must select an architecture that balances efficient resource utilization with strong tenant isolation. The objective is to balance the benefits of shared infrastructure with the demands of security, performance, and operational control.
Below are the types of Kubernetes multi-tenancy architecture.
In a soft isolation model, tenants share the same physical infrastructure but remain logically separated, relying on Kubernetes’ built-in mechanisms such as namespaces, RBAC, and resource quotas to maintain isolation. The assumption is that tenants can trust one another and that their workloads will not overlap.
Namespaces are the most popular method for logical separation in this model. About 88% of organizations now use namespaces to separate applications and workloads, compared with 65% using separate clusters.
Key characteristics include:
Typical Use Case: Soft isolation is commonly used in trusted environments where tenants are part of the same organization or have a high degree of trust between them. It works well in smaller environments or when resource efficiency is a priority, but strict security boundaries are not required.
Soft isolation works for trusted tenants, but if workloads involve untrusted or externally managed tenants, soft isolation can introduce security blind spots.
In a hard isolation model, tenants are treated as completely untrusted, requiring stronger isolation and security between workloads. This approach ensures that even if one tenant’s workload is compromised, it cannot impact other tenants.
Key characteristics include:
Typical Use Case: Hard isolation is suitable for untrusted environments where tenants are independent organizations or third-party customers. It is critical in scenarios requiring strong performance guarantees, security, or regulatory compliance, such as multi-tenant SaaS platforms, financial institutions, or healthcare applications.
Hard isolation adds overhead but is often mandatory in finance or healthcare environments where SLAs and compliance are critical.
Once you understand the different types of Kubernetes multi-tenancy architectures, it’s helpful to look at the practical ways to set up multi-tenancy in clusters.
In Kubernetes, there are several architectural approaches to implementing multi-tenancy, each with trade-offs in resource isolation, security, management overhead, and scalability. Here are the key models for setting up multi-tenancy in Kubernetes clusters:
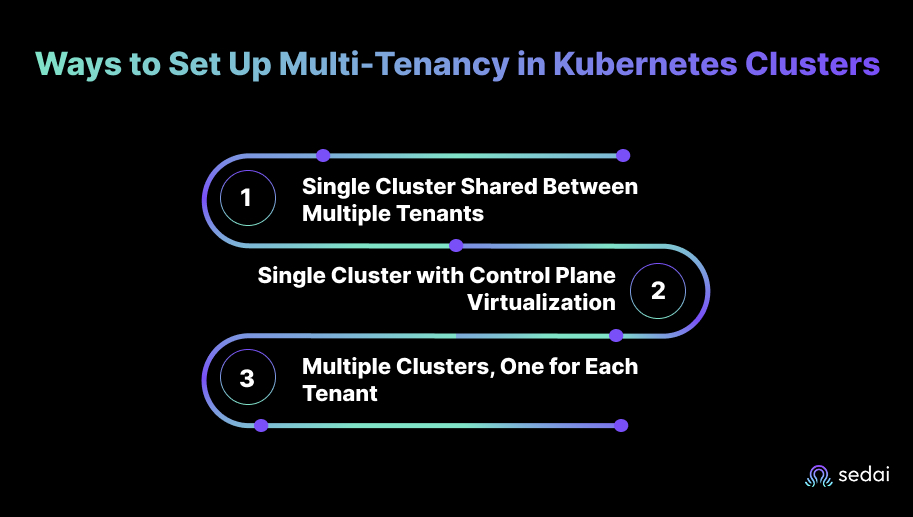
In this model, multiple tenants share a single Kubernetes cluster, with resources such as CPU, memory, and storage pooled across tenants. Logical isolation is achieved using namespaces, while resource limits and access control policies help ensure tenants do not interfere with each other.
Use Case: Ideal for trusted environments, such as internal teams or departments within the same organization, where strict security requirements are not critical.
This approach uses a single Kubernetes cluster with control plane virtualization. Each tenant operates within a virtual cluster, providing isolation for control plane resources while sharing the same physical infrastructure.
Use Case: Suitable for organizations that want multi-cluster management benefits without the overhead of fully separate clusters. Ideal for large teams needing flexibility to manage their cluster configurations while leveraging shared infrastructure.
In this model, each tenant receives a dedicated Kubernetes cluster, providing complete isolation. Workloads from different tenants run in entirely separate clusters, ensuring maximum security and independence.
Use Case: Best for highly regulated environments, such as SaaS providers or organizations with strict compliance requirements (e.g., healthcare, finance), where tenants require full isolation from each other.
Once you’re familiar with the setup methods, adopting best practices can help maintain effective and secure multi-tenancy.
Also Read: Kubernetes Cluster Scaling Challenges
To build an efficient, secure, and scalable multi-tenant Kubernetes environment, you need to adopt advanced practices that go beyond basic cluster configuration. The following best practices focus on tenant management, security optimization, and performance scalability, ensuring that multi-tenancy scales effectively.
Integrate OIDC with identity providers like LDAP, Active Directory, or OAuth2 to enforce fine-grained tenant-level access control. Pair this with Kubernetes RBAC to restrict access to namespaces and resources based on authenticated identities.
Implement tenant-specific authentication rules and enforce least-privilege access. Introduce multi-factor authentication (MFA) for sensitive workloads to further improve security.
Configure StorageClasses to define IOPS or throughput requirements per tenant. Use Persistent Volume Claims (PVCs) to align storage with tenant-specific performance needs.
Implement dynamic provisioning with storage classes and enforce quotas to prevent over-allocation, optimizing storage efficiency across tenants.
Use tools for tenant-level backups, ensuring workloads and data are independently recoverable. Implement namespace-level backup policies for isolation and reliability.
Test disaster recovery procedures regularly for each tenant, automate backups, and align recovery with tenant-specific SLAs to ensure rapid, reliable restoration.
Use tenant-specific labels to segregate logs and metrics. Encrypt logs in transit and at rest, and routinely verify retention policies to maintain compliance with standards like GDPR or HIPAA.
Must Read: Top Kubernetes Cost Optimization Tools for 2026
Multi-tenant Kubernetes environments demand constant attention. Teams need to keep tenants isolated, ensure workloads scale fairly, and prevent noisy-neighbor performance issues. Manual monitoring and tuning often fall short, especially as workloads evolve faster than engineers can respond.
This is where Sedai steps in. By learning how Kubernetes workloads behave over time, forecasting demand, and applying safe, autonomous optimizations, Sedai prevents tenant conflicts before they occur. Instead of reacting to problems, it proactively adjusts compute, memory, and scaling parameters so shared clusters remain stable and efficient.
Here’s how Sedai improves multi-tenant Kubernetes operations:
With Sedai, multi-tenant Kubernetes clusters remain efficient without requiring engineers to monitor every namespace, workload, or contention event. Clusters stay balanced, workloads remain responsive, and operational risk decreases because optimization happens continuously rather than reactively.
Successfully managing a multi-tenant Kubernetes environment is about building a resilient system that scales efficiently while providing the flexibility and security each tenant needs.
By focusing on proactive management, you can prevent pitfalls and optimize performance over time. It also ensures your Kubernetes clusters stay resilient, secure, and cost-effective as your organization grows. That's where Autonomous solutions like Sedai simplify multi-tenant Kubernetes management.
By monitoring workload behavior in real time, predicting resource needs, and automating scaling and optimization, Sedai keeps your clusters performing at their best while maintaining security, all without constant manual intervention.
Gain full control of your Kubernetes environment and achieve efficiency, security, and cost savings at scale.
A1. Combine resource quotas, network policies, and dedicated node pools to balance isolation and performance. Resource quotas allocate CPU and memory fairly, while network policies control inter-tenant communication. HPA and VPA ensure each tenant gets the resources it needs without affecting others.
A2. Regularly review usage and implement HPA/VPA to prevent over-provisioning. Integrating cloud-native billing tools such as AWS Cost Explorer or Azure Cost Management with Kubernetes billing tags provides deeper visibility into tenant-specific costs.
A3. Combine Cluster Autoscaler, dedicated node pools, and tenant-specific scaling policies. Cluster Autoscaler adjusts node counts based on demand, while dedicated node pools prevent high-demand tenants from affecting others. HPA and VPA at the pod level scale workloads according to real-time demand.
A4. Use Role-Based Access Control (RBAC) to limit namespace access and PodSecurityPolicies to restrict tenant permissions. Network segmentation with tools enhances isolation, and service meshes such as Istio secure inter-tenant communication with mTLS.
A5. Yes, but strict compliance is required. Implement hard isolation with dedicated node pools, advanced security policies, and service meshes for secure communication. Conduct regular security audits, enforce multi-factor authentication (MFA), and ensure data encryption at rest and in transit to comply with regulations like HIPAA or GDPR.
December 9, 2025
December 9, 2025

Managing multi-tenant Kubernetes clusters requires a deep understanding of resource allocation, security, and scaling strategies. Proper isolation through namespaces, RBAC (Role-Based Access Control), and network policies is crucial to prevent resource contention and security risks. Implementing autoscaling mechanisms for both pods and nodes can optimize resource usage across tenants. Additionally, effective monitoring and logging solutions provide visibility into resource consumption, ensuring fair distribution, preventing overprovisioning, and optimizing costs.
Running multiple tenants in the same Kubernetes cluster seems efficient at first glance, but in reality, it often exposes performance, security, and cost challenges quickly. Teams expect consolidation to simplify operations, yet they end up dealing with tenants competing for CPU, noisy-neighbor effects, and gaps in policies that weaken isolation.
The issue is common across the industry. According to the 2024 CNCF report, 93% of organizations are using or evaluating Kubernetes, but multi-tenant environments still struggle with resource contention, uneven scaling, and configuration drift.
These problems add operational risk and unnecessary cloud spend unless you control how tenants share and consume cluster resources. This is where solid multi-tenant design principles make a real difference.
By understanding the limitations of multi-tenant Kubernetes and applying the right solutions, you can reduce complexity, lower risk, and improve overall efficiency. In this blog, you'll explore how to make multi-tenant Kubernetes work effectively for your organization.
Kubernetes multi-tenancy is the practice of running multiple workloads or applications from different teams or customers (tenants) within a single Kubernetes cluster, while maintaining strict logical isolation and independent resource management for each tenant.

This model allows organizations to share infrastructure efficiently, improving utilization and reducing operational overhead. At the same time, it demands strong security, resource allocation, and workload isolation strategies to ensure performance and reliability are not compromised.
For example, internal SaaS platforms often consolidate multiple teams on a single cluster to reduce costs. But without proper isolation and quotas, one team’s experiments can spike CPU usage, slowing production workloads.
Here’s why Kubernetes multi-latency matters:
In multi-tenant Kubernetes, tenants share a single cluster while remaining logically isolated via namespaces. Each namespace allows independent management of resources like CPU and memory, but Kubernetes does not enforce strict isolation by default.
You must configure resource quotas, limit ranges, and RBAC to prevent tenants from interfering with each other’s resources or security.
Resource allocation is critical in a multi-tenant Kubernetes environment to prevent any tenant from consuming disproportionate resources. You should set resource requests and limits on containers and define quotas per namespace to prevent contention. Without these controls, tenants can unintentionally impact each other’s performance.
Sharing infrastructure introduces security challenges in multi-tenant Kubernetes. Implementing RBAC ensures that tenants access only their own resources, while network policies isolate pod-to-pod communication.
PodSecurityPolicies enforce container security, such as preventing privileged containers. You must rigorously configure these policies to prevent unauthorized access and maintain robust security.
Performance can degrade if tenants over-consume resources. You can optimize workloads with Horizontal Pod Autoscaling (HPA) and Vertical Pod Autoscaling (VPA), which automatically adjust resources based on demand.
Cluster autoscalers allow the cluster to add or remove nodes as needed. Proper scaling strategies maintain performance while avoiding resource waste.
Monitoring is essential to track resource usage and ensure tenants stay within limits. Using tools, you can create tenant-specific dashboards for metrics such as CPU, memory, and network usage.
Centralized logging with ELK Stack or similar solutions helps detect issues, enforce resource limits, and ensure smooth operation across tenants.
Once you understand the importance of Kubernetes multi-tenancy, it’s useful to examine the challenges it presents and the solutions available to address them.
Implementing Kubernetes in a multi-tenant environment delivers significant benefits in resource optimization and cost efficiency, but it also introduces challenges and limitations. You need to understand the key obstacles and know how to address them effectively for maintaining performance, security, and scalability.
In multi-tenant Kubernetes clusters, resource contention is a critical challenge. When tenants share the same physical infrastructure, workloads from different tenants can compete for CPU, memory, and storage, potentially degrading performance if they are not properly isolated or allocated.
Key solutions include:
Monitoring pod-level resource usage and node-level metrics helps identify noisy tenants before they degrade cluster performance.
Although Kubernetes provides logical isolation via namespaces, sharing physical resources introduces security risks. A compromised tenant could affect other tenants if proper isolation measures are not enforced. Ensuring strong security across all tenants is vital to prevent unauthorized access and workload interference.
Key solutions include:
Even with service mesh, misconfigurations in RBAC or network policies can allow lateral movement. Continuous audits are essential.
Providing visibility into resource usage, performance, and security for each tenant is challenging in multi-tenant environments. Without effective monitoring, bottlenecks or security issues can go undetected, potentially leading to operational disruptions or breaches.
Key solutions include:
Scaling a multi-tenant Kubernetes cluster requires balancing multiple tenants’ demands with available resources. As workloads fluctuate, you must scale efficiently without over-provisioning or compromising performance.
Key solutions include:
Avoid scaling too aggressively without monitoring actual usage, as over-provisioning leads to wasted costs and unnecessary operational complexity.
Multi-tenant Kubernetes clusters introduce operational overhead, especially as the number of tenants grows. Maintaining consistency and preventing configuration drift becomes increasingly challenging.
Key solutions include:
Tracking and allocating costs across tenants in a multi-tenant cluster can be complex. Without visibility, some tenants may consume disproportionate resources, causing unexpected cost spikes.
Key solutions included:
Assigning tenant-level chargeback or showback reports encourages teams to optimize their workloads and prevents hidden overspend.
After understanding the challenges and solutions of multi-tenant Kubernetes, it’s helpful to compare single tenancy and multi-tenancy to see how they differ.
Suggested Read: Buyer’s Guide to Kubernetes Optimization
Single-tenancy in Kubernetes provides complete isolation but comes with higher infrastructure overhead and potential resource underutilization. Multi-tenancy, on the other hand, allows resource sharing, improving cost efficiency and scalability, but demands strict controls to prevent security risks and performance issues.
Below are the key differences between single-tenancy and multi-tenancy.
While multi-tenancy reduces infrastructure costs, the operational overhead and need for strong monitoring often outweigh savings for small environments. Evaluate trade-offs before consolidating clusters.
Once you are clear about the differences between single and multi-tenancy, you need to have a look at the different types of multi-tenancy architecture.
When configuring multi-tenancy in Kubernetes, you must select an architecture that balances efficient resource utilization with strong tenant isolation. The objective is to balance the benefits of shared infrastructure with the demands of security, performance, and operational control.
Below are the types of Kubernetes multi-tenancy architecture.
In a soft isolation model, tenants share the same physical infrastructure but remain logically separated, relying on Kubernetes’ built-in mechanisms such as namespaces, RBAC, and resource quotas to maintain isolation. The assumption is that tenants can trust one another and that their workloads will not overlap.
Namespaces are the most popular method for logical separation in this model. About 88% of organizations now use namespaces to separate applications and workloads, compared with 65% using separate clusters.
Key characteristics include:
Typical Use Case: Soft isolation is commonly used in trusted environments where tenants are part of the same organization or have a high degree of trust between them. It works well in smaller environments or when resource efficiency is a priority, but strict security boundaries are not required.
Soft isolation works for trusted tenants, but if workloads involve untrusted or externally managed tenants, soft isolation can introduce security blind spots.
In a hard isolation model, tenants are treated as completely untrusted, requiring stronger isolation and security between workloads. This approach ensures that even if one tenant’s workload is compromised, it cannot impact other tenants.
Key characteristics include:
Typical Use Case: Hard isolation is suitable for untrusted environments where tenants are independent organizations or third-party customers. It is critical in scenarios requiring strong performance guarantees, security, or regulatory compliance, such as multi-tenant SaaS platforms, financial institutions, or healthcare applications.
Hard isolation adds overhead but is often mandatory in finance or healthcare environments where SLAs and compliance are critical.
Once you understand the different types of Kubernetes multi-tenancy architectures, it’s helpful to look at the practical ways to set up multi-tenancy in clusters.
In Kubernetes, there are several architectural approaches to implementing multi-tenancy, each with trade-offs in resource isolation, security, management overhead, and scalability. Here are the key models for setting up multi-tenancy in Kubernetes clusters:

In this model, multiple tenants share a single Kubernetes cluster, with resources such as CPU, memory, and storage pooled across tenants. Logical isolation is achieved using namespaces, while resource limits and access control policies help ensure tenants do not interfere with each other.
Use Case: Ideal for trusted environments, such as internal teams or departments within the same organization, where strict security requirements are not critical.
This approach uses a single Kubernetes cluster with control plane virtualization. Each tenant operates within a virtual cluster, providing isolation for control plane resources while sharing the same physical infrastructure.
Use Case: Suitable for organizations that want multi-cluster management benefits without the overhead of fully separate clusters. Ideal for large teams needing flexibility to manage their cluster configurations while leveraging shared infrastructure.
In this model, each tenant receives a dedicated Kubernetes cluster, providing complete isolation. Workloads from different tenants run in entirely separate clusters, ensuring maximum security and independence.
Use Case: Best for highly regulated environments, such as SaaS providers or organizations with strict compliance requirements (e.g., healthcare, finance), where tenants require full isolation from each other.
Once you’re familiar with the setup methods, adopting best practices can help maintain effective and secure multi-tenancy.
Also Read: Kubernetes Cluster Scaling Challenges
To build an efficient, secure, and scalable multi-tenant Kubernetes environment, you need to adopt advanced practices that go beyond basic cluster configuration. The following best practices focus on tenant management, security optimization, and performance scalability, ensuring that multi-tenancy scales effectively.
Integrate OIDC with identity providers like LDAP, Active Directory, or OAuth2 to enforce fine-grained tenant-level access control. Pair this with Kubernetes RBAC to restrict access to namespaces and resources based on authenticated identities.
Implement tenant-specific authentication rules and enforce least-privilege access. Introduce multi-factor authentication (MFA) for sensitive workloads to further improve security.
Configure StorageClasses to define IOPS or throughput requirements per tenant. Use Persistent Volume Claims (PVCs) to align storage with tenant-specific performance needs.
Implement dynamic provisioning with storage classes and enforce quotas to prevent over-allocation, optimizing storage efficiency across tenants.
Use tools for tenant-level backups, ensuring workloads and data are independently recoverable. Implement namespace-level backup policies for isolation and reliability.
Test disaster recovery procedures regularly for each tenant, automate backups, and align recovery with tenant-specific SLAs to ensure rapid, reliable restoration.
Use tenant-specific labels to segregate logs and metrics. Encrypt logs in transit and at rest, and routinely verify retention policies to maintain compliance with standards like GDPR or HIPAA.
Must Read: Top Kubernetes Cost Optimization Tools for 2026
Multi-tenant Kubernetes environments demand constant attention. Teams need to keep tenants isolated, ensure workloads scale fairly, and prevent noisy-neighbor performance issues. Manual monitoring and tuning often fall short, especially as workloads evolve faster than engineers can respond.
This is where Sedai steps in. By learning how Kubernetes workloads behave over time, forecasting demand, and applying safe, autonomous optimizations, Sedai prevents tenant conflicts before they occur. Instead of reacting to problems, it proactively adjusts compute, memory, and scaling parameters so shared clusters remain stable and efficient.
Here’s how Sedai improves multi-tenant Kubernetes operations:
With Sedai, multi-tenant Kubernetes clusters remain efficient without requiring engineers to monitor every namespace, workload, or contention event. Clusters stay balanced, workloads remain responsive, and operational risk decreases because optimization happens continuously rather than reactively.
Successfully managing a multi-tenant Kubernetes environment is about building a resilient system that scales efficiently while providing the flexibility and security each tenant needs.
By focusing on proactive management, you can prevent pitfalls and optimize performance over time. It also ensures your Kubernetes clusters stay resilient, secure, and cost-effective as your organization grows. That's where Autonomous solutions like Sedai simplify multi-tenant Kubernetes management.
By monitoring workload behavior in real time, predicting resource needs, and automating scaling and optimization, Sedai keeps your clusters performing at their best while maintaining security, all without constant manual intervention.
Gain full control of your Kubernetes environment and achieve efficiency, security, and cost savings at scale.
A1. Combine resource quotas, network policies, and dedicated node pools to balance isolation and performance. Resource quotas allocate CPU and memory fairly, while network policies control inter-tenant communication. HPA and VPA ensure each tenant gets the resources it needs without affecting others.
A2. Regularly review usage and implement HPA/VPA to prevent over-provisioning. Integrating cloud-native billing tools such as AWS Cost Explorer or Azure Cost Management with Kubernetes billing tags provides deeper visibility into tenant-specific costs.
A3. Combine Cluster Autoscaler, dedicated node pools, and tenant-specific scaling policies. Cluster Autoscaler adjusts node counts based on demand, while dedicated node pools prevent high-demand tenants from affecting others. HPA and VPA at the pod level scale workloads according to real-time demand.
A4. Use Role-Based Access Control (RBAC) to limit namespace access and PodSecurityPolicies to restrict tenant permissions. Network segmentation with tools enhances isolation, and service meshes such as Istio secure inter-tenant communication with mTLS.
A5. Yes, but strict compliance is required. Implement hard isolation with dedicated node pools, advanced security policies, and service meshes for secure communication. Conduct regular security audits, enforce multi-factor authentication (MFA), and ensure data encryption at rest and in transit to comply with regulations like HIPAA or GDPR.