Unlock the Full Value of FinOps
By enabling safe, continuous optimization under clear policies and guardrails

December 17, 2025
June 17, 2025
December 17, 2025
June 17, 2025

Whether you’re a CTO, a recent engineering grad, or somewhere in between, you need to know how to safely store and manage your company’s secrets.
Today, many companies solve this challenge with AWS Secrets Manager. The tool helps engineers secure sensitive data, such as credentials, API keys, and OAuth tokens. Let’s explore how it helps you meet compliance standards and removes the overhead of secret management in cloud environments.
Hard-coded secrets are a ticking time bomb. Your team might know it, yet they're still buried in code, scripts, and YAML files. Every exposed token or forgotten API key is a potential security incident waiting to happen. And the pressure to "just ship it" doesn't leave much room for manual rotation or patchwork vault systems.
This is how AWS Secrets Manager can help you with it.
Secrets Manager stores things like:
All encrypted, all safe, no more grepping through repos to check what's exposed.
Your applications don't need to know secrets in advance. They fetch them securely at runtime, reducing your attack surface and removing the need for hard-coded values in:
Secrets Manager can automatically rotate credentials on a schedule you define. That means fewer operational headaches and no last-minute scrambles to rotate access keys after an engineer leaves.
You get:
You don’t need another security headache or another spreadsheet of credentials. If you’re like most SREs, DevOps engineers, or platform owners, you're already juggling enough fire drills.
Credentials scattered across repos, environment variables, and sticky notes (we see you) only add risk, complexity, and manual overhead. That’s where AWS Secrets Manager can help, if you know what to store and what to skip.
AWS Secrets Manager is built to manage sensitive data safely and centrally. You can store:
This flexibility means you can store a wide range of secrets, but that doesn’t mean you should store everything here.
Some secrets are better handled by purpose-built AWS services. Here's what to offload elsewhere:
Secrets Manager is powerful, but knowing when to use it (and when not to) saves you both risk and cost. Next, let’s break down who can actually use Secrets Manager, and how access works.
If managing secrets feels like a never-ending game of hide-and-seek, you're not alone. From lost credentials to manual rotations, the process eats up time, increases risk, and adds stress you just don’t need. Secrets Manager is here to change that for every role that touches security, uptime, or speed.
This isn't just a tool for one team. It's built to work across your org, streamlining how secrets are stored, rotated, and secured, so you can stop chasing issues and start scaling with confidence.
Tired of juggling a dozen vaults and sticky notes? Secrets Manager gives you a centralized, automated system to manage secrets—no more risky manual updates or last-minute fire drills.
You’re on the hook for compliance and audit-readiness. Secrets Manager helps you stay one step ahead, without needing an army of analysts.
Your job is to ship code, not worry about embedded API keys or rotating database passwords. Secrets Manager lets you stay focused on building, while it keeps your secrets safe.
Secrets Manager helps your entire team move faster and sleep better. Next, let's look at why using a secret manager is a no-brainer.
Hardcoding secrets into your app or CI/CD pipeline isn’t just risky, it’s asking for a breach. Your team will have more valuable tasks at hand than chasing down expired credentials or troubleshooting mystery 500s caused by missing API keys.
With AWS Secrets Manager, it actually can be.
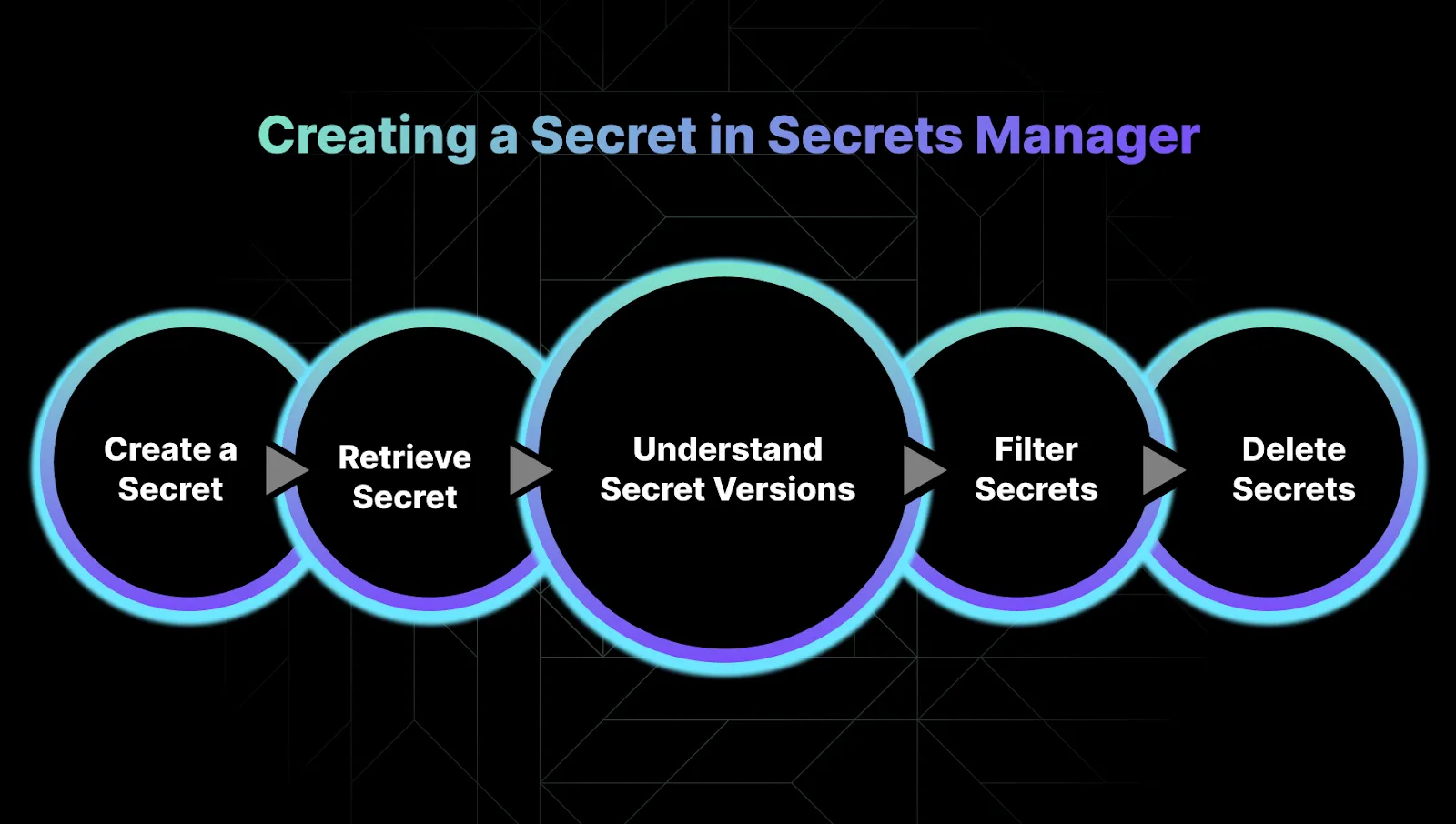
Here’s how to create and manage secrets without breaking a sweat.
You’ve got options, GUI or CLI. Pick what fits your workflow:
Via the AWS Console
Done in a few clicks.
Via the CLI (for the automation-first crowd)
aws secretsmanager create-secret \
--name MyTestSecret2 \
--description "My test secret created with the CLI." \
--secret-string "{'user':'tiexin','password':'EXAMPLE-PASSWORD'}"Prefer to keep things clean in a JSON file? No problem.
1. Create a file called mycreds.json:
{
"username": "tiexin",
"password": "EXAMPLE-PASSWORD"
}2. Use it to create a secret:
aws secretsmanager create-secret \
--name MyTestSecret3 \
--secret-string file://mycreds.json
Get the value of your secret:
aws secretsmanager get-secret-value --secret-id MyTestSecret3Update the secret:
aws secretsmanager put-secret-value \
--secret-id MyTestSecret3 \
--secret-string "{\"user\":\"tiexin\",\"password\":\"EXAMPLE-PASSWORD\"}"Each update creates a new version, which is helpful when you need to roll back.
AWS Secrets Manager tracks secret versions with labels:
List versions like this:
aws secretsmanager list-secret-version-ids --secret-id MyTestSecret3The version labeling system keeps your secrets secure and rollbacks easy—no need to manage a version history manually.
You can list all your secrets or filter them.
List all secrets:
aws secretsmanager list-secretsFilter by name prefix:
aws secretsmanager list-secrets --filter Key="name",Values="MyTest"Other useful filters include:
Deleting a secret isn’t instant, and that’s a good thing.
Schedule a deletion witha recovery window:
aws secretsmanager delete-secret \
--secret-id MyTestSecret3 \
--recovery-window-in-days 7
Recover a scheduled deletion:
aws secretsmanager restore-secret \
--secret-id MyTestSecret3Need to delete immediately? Only if you know what you're doing:
aws secretsmanager delete-secret \
--secret-id MyTestSecret2 \
--force-delete-without-recovery
Next, we'll look at how to manage access and permissions for your secrets safely and efficiently.
Now that your secrets are safely stored and set up, it’s time to put them to work. You’ll want your applications to fetch these secrets securely, without exposing them in your code or configuration files. One common way to do this is by accessing Secrets Manager directly through AWS SDKs, letting your app retrieve secrets at runtime with minimal hassle.
1. From Applications Directly Using SDK
For example, to access secrets from a Python application, you will need:
To install the component, use the following command.
$ pip install aws-secretsmanager-cachingThe Python application needs the following IAM permissions:
For example, if you are running the Python app on an EC2 virtual machine, the instace profile of that EC2 needs the above permissions.
The following code snippet example shows how to get the secret value for a secret named MyTestSecret1:
import botocore
import botocore.session
from aws_secretsmanager_caching import SecretCache, SecretCacheConfig
client = botocore.session.get_session().create_client('secretsmanager')
cache_config = SecretCacheConfig()
cache = SecretCache( config = cache_config, client = client)
secret = cache.get_secret_string('MyTestSecret1')
print(secret)
2. From CI Workflows (Example: GitHub Actions)
We can use a secret in a GitHub job to retrieve secrets from AWS Secrets Manager and add them as masked Environment variables in our GitHub workflows.
To do this, you first need to allow GitHub Actions to access AWS Secrets Manager, which can be achieved by using the GitHub OIDC provider. The IAM role assumed by the GitHub Actions must have the following permissions:
Then you can simply add a step in our GitHub Actions workflow using the following syntax to access secrets from Secrets Manager:
- name: Step name
uses: aws-actions/aws-secretsmanager-get-secrets@v1
with:
secret-ids: MyTestSecret1
parse-json-secrets: (Optional) true|false
3. From K8s/EKS Clusters with the Secret Provider Class (SPC)
Similarly, you can use the Kubernetes Secret Provider Class to access secrets from Kubernetes clusters.
We use YAML to describe which secrets to mount in AWS EKS. The SPC is in the following format:
apiVersion: secrets-store.csi.x-k8s.io/v1
kind: SecretProviderClass
metadata:
name: <NAME>
spec:
provider: aws
parameters:
region:
failoverRegion:
pathTranslation:
objects:Here's an example:
apiVersion: secrets-store.csi.x-k8s.io/v1alpha1
kind: SecretProviderClass
metadata:
name: nginx-deployment-aws-secrets
spec:
provider: aws
parameters:
objects: |
- objectName: "MySecret"
objectType: "secretsmanager"With the fundamentals of secret management in place, it’s time to simplify the key operations. Below is a quick-reference cheat sheet to help you rotate and access secrets efficiently using AWS Secrets Manager.
Managing secrets should never feel like a guessing game or a manual headache. If you’re a CTO, SRE, DevOps, or Platform Engineer, you know that handling secrets safely and efficiently is mission critical, but often time-consuming and error-prone. This quick-reference cheat sheet gets you straight to the essentials for rotating and accessing secrets with AWS Secrets Manager, so you can keep your applications secure without the stress.
1. Secrets CRUD
Create:
aws secretsmanager create-secret --name MyTestSecret \
--description "xxx" \
--secret-string "xxx"
Create using a file:
aws secretsmanager create-secret \
--name MyTestSecret \
--secret-string file://mycreds.json
Read:
aws secretsmanager get-secret-value --secret-id MyTestSecret
Update:
aws secretsmanager put-secret-value \
--secret-id MyTestSecret \
--secret-string "yyy"
List versions:
aws secretsmanager list-secret-version-ids --secret-id MyTestSecret
List/search:
aws secretsmanager list-secrets --filter Key="name",Values="MyTest"
Delete:
aws secretsmanager delete-secret \
--secret-id MyTestSecret \
--recovery-window-in-days 7
Force delete without a recovery window:
aws secretsmanager delete-secret \
--secret-id MyTestSecret \
--force-delete-without-recovery
2. Access Secrets from GitHub Actions
GitHub Actions step to read a secret:
- name: Step name
uses: aws-actions/aws-secretsmanager-get-secrets@v1
with:
secret-ids: MyTestSecret1
parse-json-secrets: (Optional) true|false
If you're managing secrets at scale, guessing your AWS Secrets Manager bill can feel like a gamble. You want clear pricing without hidden fees or surprise charges that throw your budget off. AWS Secrets Manager pricing is simple, transparent, and tied directly to what you use, no upfront contracts or extra licensing fees.
AWS charges based on two things:
You don’t pay for the underlying infrastructure or extra personnel to keep secrets safe and accessible. That’s all baked in.
AWS offers a 30-day free trial starting when you store your first secret. Use this period to test secret rotation, retrieval, and management at no cost.
Want to see how Secrets Manager fits into your overall architecture budget? The AWS Pricing Calculator helps you build a custom estimate tailored to your usage.
To help you understand costs in action, here are some typical scenarios:
1. Production-Scale Web App
2. Microservices with Ephemeral Secrets
3. Teams Spending $40K+ Monthly on AWS
4. Teams Spending $250K+ Monthly on AWS
If your secret volume or API calls are very high, consider contacting AWS for custom pricing options.
Understanding these numbers helps you plan better and avoid surprises. Next, we'll explore how sedai enhances secret management to get the most value from your spend.
Managing secrets is about keeping your cloud secure without draining your team’s time or your budget. Sedai works hand-in-hand with AWS Secrets Manager to make your secrets management smarter, safer, and cost-efficient.
Sedai connects seamlessly with your AWS cloud environment to optimize and manage your resources securely and efficiently, without the manual toil.
Hardcoded secrets are a ticking time bomb. You know the risks, exposure, breaches, and endless manual rotations. AWS Secrets Manager takes that headache away by securing your credentials and automating rotation and access control.
But as your cloud footprint grows, keeping governance tight and costs in check gets tougher. Pairing Sedai with AWS Secrets Manager lets you automate cloud cost optimization without risking security or performance.
Join us and cut your cloud spend by up to 50% while keeping credentials safe and sound.
1. How does AWS Secrets Manager improve security?
AWS Secrets Manager centralizes credential storage with encryption, automatic rotation, and fine-grained access controls, removing the need for hardcoded secrets in applications or scripts.
2. Can Sedai reduce the costs associated with secrets management?
Yes. Sedai can help teams eliminate additional usage by restricting and automating cloud usage as per requirement, without compromising security.
3. What types of secrets work best in AWS Secrets Manager?
Database credentials, API keys, and service account passwords are ideal. For AWS-specific credentials (like IAM keys) or certificates, consider using IAM or AWS Certificate Manager instead.
4. Is Secrets Manager suitable for hybrid or multi-cloud environments?
While designed for AWS, Secrets Manager can store credentials for on-premises or third-party services.
June 17, 2025
December 17, 2025

Whether you’re a CTO, a recent engineering grad, or somewhere in between, you need to know how to safely store and manage your company’s secrets.
Today, many companies solve this challenge with AWS Secrets Manager. The tool helps engineers secure sensitive data, such as credentials, API keys, and OAuth tokens. Let’s explore how it helps you meet compliance standards and removes the overhead of secret management in cloud environments.
Hard-coded secrets are a ticking time bomb. Your team might know it, yet they're still buried in code, scripts, and YAML files. Every exposed token or forgotten API key is a potential security incident waiting to happen. And the pressure to "just ship it" doesn't leave much room for manual rotation or patchwork vault systems.
This is how AWS Secrets Manager can help you with it.
Secrets Manager stores things like:
All encrypted, all safe, no more grepping through repos to check what's exposed.
Your applications don't need to know secrets in advance. They fetch them securely at runtime, reducing your attack surface and removing the need for hard-coded values in:
Secrets Manager can automatically rotate credentials on a schedule you define. That means fewer operational headaches and no last-minute scrambles to rotate access keys after an engineer leaves.
You get:
You don’t need another security headache or another spreadsheet of credentials. If you’re like most SREs, DevOps engineers, or platform owners, you're already juggling enough fire drills.
Credentials scattered across repos, environment variables, and sticky notes (we see you) only add risk, complexity, and manual overhead. That’s where AWS Secrets Manager can help, if you know what to store and what to skip.
AWS Secrets Manager is built to manage sensitive data safely and centrally. You can store:
This flexibility means you can store a wide range of secrets, but that doesn’t mean you should store everything here.
Some secrets are better handled by purpose-built AWS services. Here's what to offload elsewhere:
Secrets Manager is powerful, but knowing when to use it (and when not to) saves you both risk and cost. Next, let’s break down who can actually use Secrets Manager, and how access works.
If managing secrets feels like a never-ending game of hide-and-seek, you're not alone. From lost credentials to manual rotations, the process eats up time, increases risk, and adds stress you just don’t need. Secrets Manager is here to change that for every role that touches security, uptime, or speed.
This isn't just a tool for one team. It's built to work across your org, streamlining how secrets are stored, rotated, and secured, so you can stop chasing issues and start scaling with confidence.

Tired of juggling a dozen vaults and sticky notes? Secrets Manager gives you a centralized, automated system to manage secrets—no more risky manual updates or last-minute fire drills.
You’re on the hook for compliance and audit-readiness. Secrets Manager helps you stay one step ahead, without needing an army of analysts.
Your job is to ship code, not worry about embedded API keys or rotating database passwords. Secrets Manager lets you stay focused on building, while it keeps your secrets safe.
Secrets Manager helps your entire team move faster and sleep better. Next, let's look at why using a secret manager is a no-brainer.

Hardcoding secrets into your app or CI/CD pipeline isn’t just risky, it’s asking for a breach. Your team will have more valuable tasks at hand than chasing down expired credentials or troubleshooting mystery 500s caused by missing API keys.
With AWS Secrets Manager, it actually can be.
Here’s how to create and manage secrets without breaking a sweat.
You’ve got options, GUI or CLI. Pick what fits your workflow:
Via the AWS Console
Done in a few clicks.
Via the CLI (for the automation-first crowd)
aws secretsmanager create-secret \
--name MyTestSecret2 \
--description "My test secret created with the CLI." \
--secret-string "{'user':'tiexin','password':'EXAMPLE-PASSWORD'}"Prefer to keep things clean in a JSON file? No problem.
1. Create a file called mycreds.json:
{
"username": "tiexin",
"password": "EXAMPLE-PASSWORD"
}2. Use it to create a secret:
aws secretsmanager create-secret \
--name MyTestSecret3 \
--secret-string file://mycreds.json
Get the value of your secret:
aws secretsmanager get-secret-value --secret-id MyTestSecret3Update the secret:
aws secretsmanager put-secret-value \
--secret-id MyTestSecret3 \
--secret-string "{\"user\":\"tiexin\",\"password\":\"EXAMPLE-PASSWORD\"}"Each update creates a new version, which is helpful when you need to roll back.
AWS Secrets Manager tracks secret versions with labels:
List versions like this:
aws secretsmanager list-secret-version-ids --secret-id MyTestSecret3The version labeling system keeps your secrets secure and rollbacks easy—no need to manage a version history manually.
You can list all your secrets or filter them.
List all secrets:
aws secretsmanager list-secretsFilter by name prefix:
aws secretsmanager list-secrets --filter Key="name",Values="MyTest"Other useful filters include:
Deleting a secret isn’t instant, and that’s a good thing.
Schedule a deletion witha recovery window:
aws secretsmanager delete-secret \
--secret-id MyTestSecret3 \
--recovery-window-in-days 7
Recover a scheduled deletion:
aws secretsmanager restore-secret \
--secret-id MyTestSecret3Need to delete immediately? Only if you know what you're doing:
aws secretsmanager delete-secret \
--secret-id MyTestSecret2 \
--force-delete-without-recovery
Next, we'll look at how to manage access and permissions for your secrets safely and efficiently.
Now that your secrets are safely stored and set up, it’s time to put them to work. You’ll want your applications to fetch these secrets securely, without exposing them in your code or configuration files. One common way to do this is by accessing Secrets Manager directly through AWS SDKs, letting your app retrieve secrets at runtime with minimal hassle.
1. From Applications Directly Using SDK
For example, to access secrets from a Python application, you will need:
To install the component, use the following command.
$ pip install aws-secretsmanager-cachingThe Python application needs the following IAM permissions:
For example, if you are running the Python app on an EC2 virtual machine, the instace profile of that EC2 needs the above permissions.
The following code snippet example shows how to get the secret value for a secret named MyTestSecret1:
import botocore
import botocore.session
from aws_secretsmanager_caching import SecretCache, SecretCacheConfig
client = botocore.session.get_session().create_client('secretsmanager')
cache_config = SecretCacheConfig()
cache = SecretCache( config = cache_config, client = client)
secret = cache.get_secret_string('MyTestSecret1')
print(secret)
2. From CI Workflows (Example: GitHub Actions)
We can use a secret in a GitHub job to retrieve secrets from AWS Secrets Manager and add them as masked Environment variables in our GitHub workflows.
To do this, you first need to allow GitHub Actions to access AWS Secrets Manager, which can be achieved by using the GitHub OIDC provider. The IAM role assumed by the GitHub Actions must have the following permissions:
Then you can simply add a step in our GitHub Actions workflow using the following syntax to access secrets from Secrets Manager:
- name: Step name
uses: aws-actions/aws-secretsmanager-get-secrets@v1
with:
secret-ids: MyTestSecret1
parse-json-secrets: (Optional) true|false
3. From K8s/EKS Clusters with the Secret Provider Class (SPC)
Similarly, you can use the Kubernetes Secret Provider Class to access secrets from Kubernetes clusters.
We use YAML to describe which secrets to mount in AWS EKS. The SPC is in the following format:
apiVersion: secrets-store.csi.x-k8s.io/v1
kind: SecretProviderClass
metadata:
name: <NAME>
spec:
provider: aws
parameters:
region:
failoverRegion:
pathTranslation:
objects:Here's an example:
apiVersion: secrets-store.csi.x-k8s.io/v1alpha1
kind: SecretProviderClass
metadata:
name: nginx-deployment-aws-secrets
spec:
provider: aws
parameters:
objects: |
- objectName: "MySecret"
objectType: "secretsmanager"With the fundamentals of secret management in place, it’s time to simplify the key operations. Below is a quick-reference cheat sheet to help you rotate and access secrets efficiently using AWS Secrets Manager.
Managing secrets should never feel like a guessing game or a manual headache. If you’re a CTO, SRE, DevOps, or Platform Engineer, you know that handling secrets safely and efficiently is mission critical, but often time-consuming and error-prone. This quick-reference cheat sheet gets you straight to the essentials for rotating and accessing secrets with AWS Secrets Manager, so you can keep your applications secure without the stress.
1. Secrets CRUD
Create:
aws secretsmanager create-secret --name MyTestSecret \
--description "xxx" \
--secret-string "xxx"
Create using a file:
aws secretsmanager create-secret \
--name MyTestSecret \
--secret-string file://mycreds.json
Read:
aws secretsmanager get-secret-value --secret-id MyTestSecret
Update:
aws secretsmanager put-secret-value \
--secret-id MyTestSecret \
--secret-string "yyy"
List versions:
aws secretsmanager list-secret-version-ids --secret-id MyTestSecret
List/search:
aws secretsmanager list-secrets --filter Key="name",Values="MyTest"
Delete:
aws secretsmanager delete-secret \
--secret-id MyTestSecret \
--recovery-window-in-days 7
Force delete without a recovery window:
aws secretsmanager delete-secret \
--secret-id MyTestSecret \
--force-delete-without-recovery
2. Access Secrets from GitHub Actions
GitHub Actions step to read a secret:
- name: Step name
uses: aws-actions/aws-secretsmanager-get-secrets@v1
with:
secret-ids: MyTestSecret1
parse-json-secrets: (Optional) true|false
If you're managing secrets at scale, guessing your AWS Secrets Manager bill can feel like a gamble. You want clear pricing without hidden fees or surprise charges that throw your budget off. AWS Secrets Manager pricing is simple, transparent, and tied directly to what you use, no upfront contracts or extra licensing fees.
AWS charges based on two things:
You don’t pay for the underlying infrastructure or extra personnel to keep secrets safe and accessible. That’s all baked in.
AWS offers a 30-day free trial starting when you store your first secret. Use this period to test secret rotation, retrieval, and management at no cost.
Want to see how Secrets Manager fits into your overall architecture budget? The AWS Pricing Calculator helps you build a custom estimate tailored to your usage.
To help you understand costs in action, here are some typical scenarios:
1. Production-Scale Web App
2. Microservices with Ephemeral Secrets
3. Teams Spending $40K+ Monthly on AWS
4. Teams Spending $250K+ Monthly on AWS
If your secret volume or API calls are very high, consider contacting AWS for custom pricing options.
Understanding these numbers helps you plan better and avoid surprises. Next, we'll explore how sedai enhances secret management to get the most value from your spend.
Managing secrets is about keeping your cloud secure without draining your team’s time or your budget. Sedai works hand-in-hand with AWS Secrets Manager to make your secrets management smarter, safer, and cost-efficient.
Sedai connects seamlessly with your AWS cloud environment to optimize and manage your resources securely and efficiently, without the manual toil.
Hardcoded secrets are a ticking time bomb. You know the risks, exposure, breaches, and endless manual rotations. AWS Secrets Manager takes that headache away by securing your credentials and automating rotation and access control.
But as your cloud footprint grows, keeping governance tight and costs in check gets tougher. Pairing Sedai with AWS Secrets Manager lets you automate cloud cost optimization without risking security or performance.
Join us and cut your cloud spend by up to 50% while keeping credentials safe and sound.
1. How does AWS Secrets Manager improve security?
AWS Secrets Manager centralizes credential storage with encryption, automatic rotation, and fine-grained access controls, removing the need for hardcoded secrets in applications or scripts.
2. Can Sedai reduce the costs associated with secrets management?
Yes. Sedai can help teams eliminate additional usage by restricting and automating cloud usage as per requirement, without compromising security.
3. What types of secrets work best in AWS Secrets Manager?
Database credentials, API keys, and service account passwords are ideal. For AWS-specific credentials (like IAM keys) or certificates, consider using IAM or AWS Certificate Manager instead.
4. Is Secrets Manager suitable for hybrid or multi-cloud environments?
While designed for AWS, Secrets Manager can store credentials for on-premises or third-party services.