Unlock the Full Value of FinOps
By enabling safe, continuous optimization under clear policies and guardrails

November 17, 2025
November 18, 2025
November 17, 2025
November 18, 2025

Integrating Amazon EC2 with Amazon VPC enables secure, isolated, and high-performance AWS environments. A well-designed VPC architecture helps engineering teams control routing, limit exposure, and scale workloads efficiently across Availability Zones. Custom VPCs improve governance and compliance, while proper subnet segmentation and IAM policies strengthen security. Combining automation and observability ensures continuous optimization of cost and performance, making EC2–VPC integration a cornerstone of modern cloud infrastructure strategy.
We’ve seen engineering teams launch hundreds of EC2 instances in record time, only to discover months later that their networking architecture can’t keep up. Instances run in default VPCs, subnets overlap across accounts, and critical workloads share public access paths meant for testing. The issue isn’t capability: AWS provides exceptional flexibility. It’s a design discipline.
According to Synergy Research Group (2024), global spending on cloud infrastructure surpassed US$330 billion, with AWS leading at roughly 31 percent market share. As adoption accelerates, so does architectural complexity. Misconfigured EC2–VPC environments now rank among the most common root causes of downtime, cost overruns, and security exposure in large-scale deployments.
This guide is written for engineering leaders and infrastructure teams who want to move beyond quick launches toward sustainable architecture. You’ll learn how to integrate EC2 instances with Amazon VPC, covering planning, configuration, connectivity, and optimization, so your environments remain secure, performant, and ready to scale.
Amazon Virtual Private Cloud (VPC) is the network layer that defines how your workloads run inside AWS. It gives you full control over IP addressing, routing, and connectivity, allowing you to design a network environment that behaves like your own data center, but with the scalability and elasticity of the cloud.
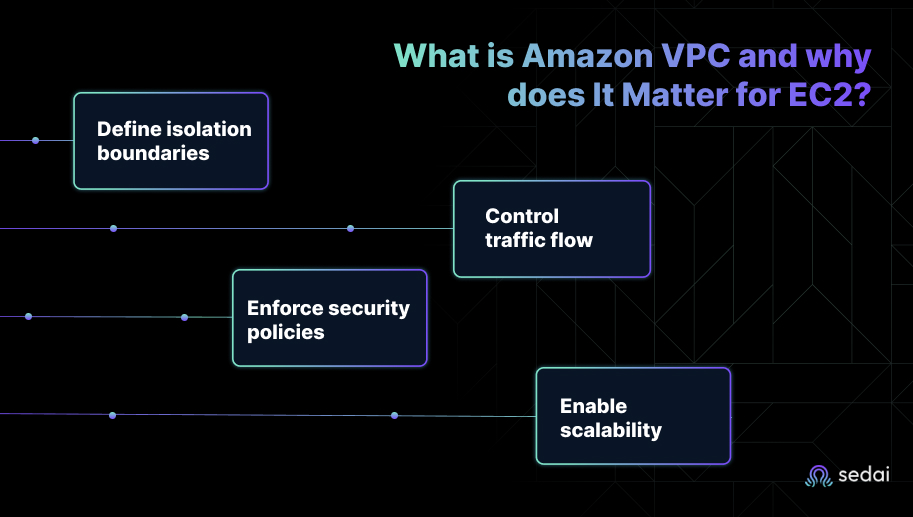
At its core, a VPC lets you:
For EC2 instances, the VPC isn’t just an attachment point: it defines performance, reachability, and compliance posture. A well-architected VPC ensures:
When teams neglect VPC design early, they often face costly reconfiguration later, overlapping CIDR blocks, conflicting routes, or under-secured public instances. A deliberate VPC layout keeps EC2 deployments predictable, secure, and easier to scale as environments grow.
Every Amazon EC2 instance must run inside a Virtual Private Cloud, but how it’s placed within that network determines how it behaves. The VPC defines the subnets, routing, and gateways that control whether an instance is reachable, private, or connected to other resources securely.
Many engineering teams start with AWS’s default VPC, which provides a quick way to launch instances with preconfigured subnets and internet access. It’s convenient for experimentation but rarely suited for production. The custom VPC, by contrast, allows you to define your own IP ranges, subnet tiers, and routing rules, ensuring security and scalability align with your architecture goals.
Key components that determine how EC2 fits into a VPC include:
In well-architected AWS environments, EC2 instances aren’t simply “launched”; they’re placed intentionally, in the right subnet, with the right routing and access controls, for their role in the system. Getting this layer right determines how easily your environment scales and how securely it operates under load.
Integrating EC2 with Amazon VPC isn’t just about connecting compute to a network. It’s about designing an environment where performance, security, and cost efficiency coexist. Each step in this process establishes a building block that affects every future deployment, from scalability to compliance visibility.
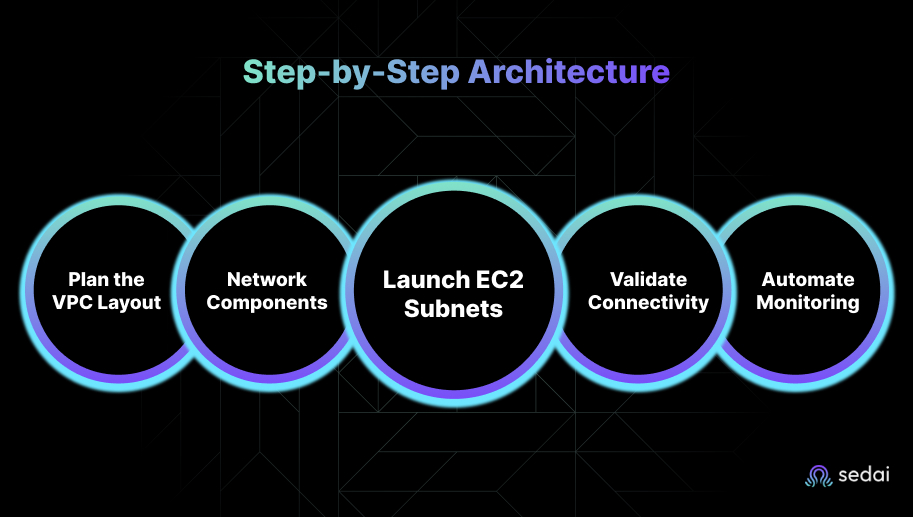
Below is a structured approach engineering teams can follow when creating a resilient EC2–VPC architecture.
Start with a clear network plan before launching any resources.
A deliberate plan prevents downstream conflicts and simplifies expansion when multiple teams share environments.
Provision the foundational networking resources:
Ensure tagging conventions align with governance or FinOps frameworks for future automation.
This step determines the network exposure and compliance posture of every instance.
After deployment, test the end-to-end traffic flow.
Validation ensures that intended network paths match operational reality before workloads scale.
Automation prevents drift, enforces consistency, and builds resilience across teams and environments.
When executed methodically, these steps transform a basic EC2-VPC setup into a scalable, governed, and fault-tolerant network fabric. The result is not just a working deployment but an architecture engineered for growth, security, and predictability.
Even the most advanced EC2 environments can fall short if the underlying VPC design isn’t intentional. The difference between a stable network and a fragile one often comes down to how consistently teams apply foundational best practices and avoid shortcuts that create operational debt later.
These principles have proven reliable across enterprise-scale AWS environments:
Avoiding these mistakes can save weeks of troubleshooting and thousands in rework:
Following these best practices transforms the VPC from a background dependency into a strategic enabler of reliability, security, and performance. Skipping them turns network architecture into a recurring firefight.
Also Read: AWS Cost Optimization: The Expert Guide (2025)
Once your EC2–VPC foundation is stable, optimization shifts from configuration to strategy. Mature AWS environments rely on advanced networking constructs that improve scalability, security, and operational control, especially across multiple teams, accounts, and regions.
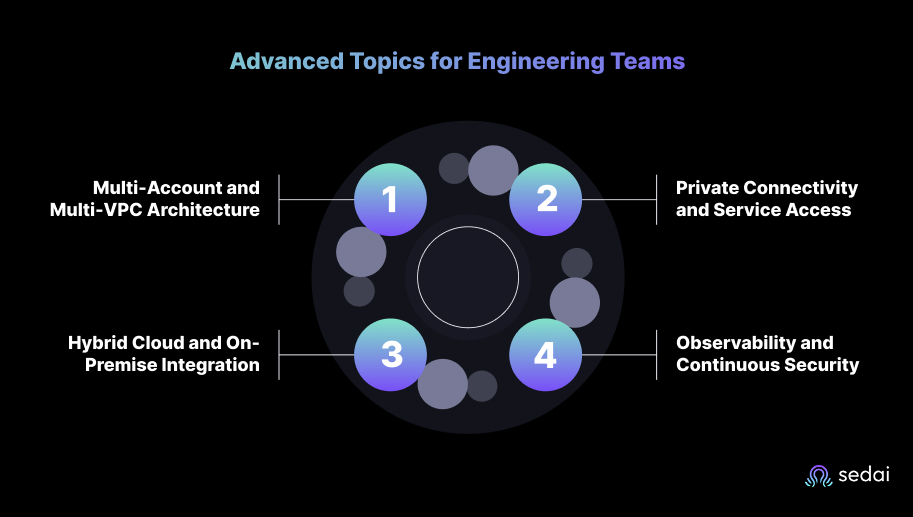
Below are the areas most engineering leaders focus on as their AWS footprint expands:
As organizations scale, a single VPC model becomes limiting. Multi-account setups using AWS Organizations and VPC Peering or Transit Gateway provide better isolation and governance.
Modern architectures reduce internet exposure by replacing public traffic with private links.
These controls reduce data transfer costs and strengthen compliance for regulated workloads.
Many engineering teams maintain hybrid workloads that span AWS and on-prem infrastructure.
As the environment grows, visibility becomes critical.
When these components are implemented thoughtfully, EC2–VPC environments evolve into robust, enterprise-grade cloud networks that are easier to secure, scale, and manage, without adding operational friction.
As AWS environments mature, manual optimization no longer scales. Engineering teams can monitor metrics, review costs, and rightsize instances, but these efforts are reactive. EC2 workloads and VPC traffic patterns shift constantly, and traditional rules or scripts rarely keep pace with changing demand. That’s why autonomous optimization has become a critical layer in modern cloud operations.
Every EC2–VPC environment must strike a balance across three priorities:
In practice, these goals often conflict. Rightsizing to cut costs can degrade performance; scaling to handle load can inflate spend. Manual tuning may work temporarily, but it introduces human latency and risk.
Sedai addresses this gap with multi-agent AI systems that continuously learn workload behavior, simulate potential changes, and act safely in production environments.
Key outcomes include:
For engineering leaders, intelligent automation means shifting from firefighting to foresight. Sedai’s approach exemplifies how EC2–VPC environments can become a self-optimizing system, adapting to demand in real time while maintaining predictable performance and compliance across workloads.
See how engineering teams measure tangible cost and performance gains with Sedai’s autonomous optimization platform: Calculate Your ROI.
Learn how Sedai optimizes AWS EC2 instances to decrease cost.
Engineering teams rarely fail because they deploy AWS incorrectly: they fail because their environments stop evolving. EC2 and VPC form the core of nearly every AWS architecture, but success depends on more than configuration. It’s the ongoing discipline of managing scale, security, and spend as workloads grow.
This is where autonomous systems now play a defining role. Platforms like Sedai bring continuous intelligence into the EC2–VPC lifecycle, ensuring that performance, availability, and cost remain balanced even as conditions evolve.
Gain full visibility into your AWS environment and reduce wasted spend immediately.
Suggested Read: Cloud Management Platforms: 2025 Buyer's Guide
Amazon EC2 provides the compute layer, virtual servers that run applications, while Amazon VPC defines the private network that those instances operate in. The VPC controls IP ranges, routing, and security, determining how each EC2 instance communicates within and outside AWS.
No. The default VPC is designed for testing and lacks fine-grained control. Production environments should use a custom VPC with structured subnets, route tables, and security groups to isolate workloads, manage traffic, and support compliance requirements.
Security begins with deliberate architecture. Sensitive workloads should run in private subnets that are not directly exposed to the internet. Access should be tightly restricted through security groups and network ACLs configured for least privilege. Every instance should use appropriate IAM roles rather than long-lived credentials, and continuous visibility should be maintained to detect and remediate anomalies in real time.
Right-size EC2 instances regularly, eliminate idle NAT gateways, and review data-transfer patterns. Automation platforms like Sedai can continuously identify and apply safe optimizations, delivering an average 30%+ reduction in cloud spend without compromising performance.
November 18, 2025
November 17, 2025

Integrating Amazon EC2 with Amazon VPC enables secure, isolated, and high-performance AWS environments. A well-designed VPC architecture helps engineering teams control routing, limit exposure, and scale workloads efficiently across Availability Zones. Custom VPCs improve governance and compliance, while proper subnet segmentation and IAM policies strengthen security. Combining automation and observability ensures continuous optimization of cost and performance, making EC2–VPC integration a cornerstone of modern cloud infrastructure strategy.
We’ve seen engineering teams launch hundreds of EC2 instances in record time, only to discover months later that their networking architecture can’t keep up. Instances run in default VPCs, subnets overlap across accounts, and critical workloads share public access paths meant for testing. The issue isn’t capability: AWS provides exceptional flexibility. It’s a design discipline.
According to Synergy Research Group (2024), global spending on cloud infrastructure surpassed US$330 billion, with AWS leading at roughly 31 percent market share. As adoption accelerates, so does architectural complexity. Misconfigured EC2–VPC environments now rank among the most common root causes of downtime, cost overruns, and security exposure in large-scale deployments.
This guide is written for engineering leaders and infrastructure teams who want to move beyond quick launches toward sustainable architecture. You’ll learn how to integrate EC2 instances with Amazon VPC, covering planning, configuration, connectivity, and optimization, so your environments remain secure, performant, and ready to scale.
Amazon Virtual Private Cloud (VPC) is the network layer that defines how your workloads run inside AWS. It gives you full control over IP addressing, routing, and connectivity, allowing you to design a network environment that behaves like your own data center, but with the scalability and elasticity of the cloud.

At its core, a VPC lets you:
For EC2 instances, the VPC isn’t just an attachment point: it defines performance, reachability, and compliance posture. A well-architected VPC ensures:
When teams neglect VPC design early, they often face costly reconfiguration later, overlapping CIDR blocks, conflicting routes, or under-secured public instances. A deliberate VPC layout keeps EC2 deployments predictable, secure, and easier to scale as environments grow.
Every Amazon EC2 instance must run inside a Virtual Private Cloud, but how it’s placed within that network determines how it behaves. The VPC defines the subnets, routing, and gateways that control whether an instance is reachable, private, or connected to other resources securely.
Many engineering teams start with AWS’s default VPC, which provides a quick way to launch instances with preconfigured subnets and internet access. It’s convenient for experimentation but rarely suited for production. The custom VPC, by contrast, allows you to define your own IP ranges, subnet tiers, and routing rules, ensuring security and scalability align with your architecture goals.
Key components that determine how EC2 fits into a VPC include:
In well-architected AWS environments, EC2 instances aren’t simply “launched”; they’re placed intentionally, in the right subnet, with the right routing and access controls, for their role in the system. Getting this layer right determines how easily your environment scales and how securely it operates under load.
Integrating EC2 with Amazon VPC isn’t just about connecting compute to a network. It’s about designing an environment where performance, security, and cost efficiency coexist. Each step in this process establishes a building block that affects every future deployment, from scalability to compliance visibility.

Below is a structured approach engineering teams can follow when creating a resilient EC2–VPC architecture.
Start with a clear network plan before launching any resources.
A deliberate plan prevents downstream conflicts and simplifies expansion when multiple teams share environments.
Provision the foundational networking resources:
Ensure tagging conventions align with governance or FinOps frameworks for future automation.
This step determines the network exposure and compliance posture of every instance.
After deployment, test the end-to-end traffic flow.
Validation ensures that intended network paths match operational reality before workloads scale.
Automation prevents drift, enforces consistency, and builds resilience across teams and environments.
When executed methodically, these steps transform a basic EC2-VPC setup into a scalable, governed, and fault-tolerant network fabric. The result is not just a working deployment but an architecture engineered for growth, security, and predictability.
Even the most advanced EC2 environments can fall short if the underlying VPC design isn’t intentional. The difference between a stable network and a fragile one often comes down to how consistently teams apply foundational best practices and avoid shortcuts that create operational debt later.
These principles have proven reliable across enterprise-scale AWS environments:
Avoiding these mistakes can save weeks of troubleshooting and thousands in rework:
Following these best practices transforms the VPC from a background dependency into a strategic enabler of reliability, security, and performance. Skipping them turns network architecture into a recurring firefight.
Also Read: AWS Cost Optimization: The Expert Guide (2025)
Once your EC2–VPC foundation is stable, optimization shifts from configuration to strategy. Mature AWS environments rely on advanced networking constructs that improve scalability, security, and operational control, especially across multiple teams, accounts, and regions.

Below are the areas most engineering leaders focus on as their AWS footprint expands:
As organizations scale, a single VPC model becomes limiting. Multi-account setups using AWS Organizations and VPC Peering or Transit Gateway provide better isolation and governance.
Modern architectures reduce internet exposure by replacing public traffic with private links.
These controls reduce data transfer costs and strengthen compliance for regulated workloads.
Many engineering teams maintain hybrid workloads that span AWS and on-prem infrastructure.
As the environment grows, visibility becomes critical.
When these components are implemented thoughtfully, EC2–VPC environments evolve into robust, enterprise-grade cloud networks that are easier to secure, scale, and manage, without adding operational friction.
As AWS environments mature, manual optimization no longer scales. Engineering teams can monitor metrics, review costs, and rightsize instances, but these efforts are reactive. EC2 workloads and VPC traffic patterns shift constantly, and traditional rules or scripts rarely keep pace with changing demand. That’s why autonomous optimization has become a critical layer in modern cloud operations.
Every EC2–VPC environment must strike a balance across three priorities:
In practice, these goals often conflict. Rightsizing to cut costs can degrade performance; scaling to handle load can inflate spend. Manual tuning may work temporarily, but it introduces human latency and risk.
Sedai addresses this gap with multi-agent AI systems that continuously learn workload behavior, simulate potential changes, and act safely in production environments.
Key outcomes include:
For engineering leaders, intelligent automation means shifting from firefighting to foresight. Sedai’s approach exemplifies how EC2–VPC environments can become a self-optimizing system, adapting to demand in real time while maintaining predictable performance and compliance across workloads.
See how engineering teams measure tangible cost and performance gains with Sedai’s autonomous optimization platform: Calculate Your ROI.
Learn how Sedai optimizes AWS EC2 instances to decrease cost.
Engineering teams rarely fail because they deploy AWS incorrectly: they fail because their environments stop evolving. EC2 and VPC form the core of nearly every AWS architecture, but success depends on more than configuration. It’s the ongoing discipline of managing scale, security, and spend as workloads grow.
This is where autonomous systems now play a defining role. Platforms like Sedai bring continuous intelligence into the EC2–VPC lifecycle, ensuring that performance, availability, and cost remain balanced even as conditions evolve.
Gain full visibility into your AWS environment and reduce wasted spend immediately.
Suggested Read: Cloud Management Platforms: 2025 Buyer's Guide
Amazon EC2 provides the compute layer, virtual servers that run applications, while Amazon VPC defines the private network that those instances operate in. The VPC controls IP ranges, routing, and security, determining how each EC2 instance communicates within and outside AWS.
No. The default VPC is designed for testing and lacks fine-grained control. Production environments should use a custom VPC with structured subnets, route tables, and security groups to isolate workloads, manage traffic, and support compliance requirements.
Security begins with deliberate architecture. Sensitive workloads should run in private subnets that are not directly exposed to the internet. Access should be tightly restricted through security groups and network ACLs configured for least privilege. Every instance should use appropriate IAM roles rather than long-lived credentials, and continuous visibility should be maintained to detect and remediate anomalies in real time.
Right-size EC2 instances regularly, eliminate idle NAT gateways, and review data-transfer patterns. Automation platforms like Sedai can continuously identify and apply safe optimizations, delivering an average 30%+ reduction in cloud spend without compromising performance.